Security Measures Are Urgently Needed to Reduce the Risk of Bankruptcy for SMEs
Date: 2021.09.15.
* 2021.09.15. Security Measures Are Urgently Needed to Reduce the Risk of Bankruptcy for SMEs
What is the Current Status of Security Measures for SMEs?

Poor Security Measures Stand Out in Small and Micro Enterprises
The Small and Medium Enterprise Agency compares the implementation status of information security measures by company size in the “Small and Medium Enterprise White Paper.” Compared to large companies, SMEs have about 20% fewer companies implementing measures, and “monitoring systems” such as the introduction of security monitoring tools are less than 50%. It is clear that security measures are not progressing in SMEs.
According to the same White Paper, information security damage occurs at a rate of approximately 1 in 6 companies, with system troubles (67.6%), computer viruses (48.6%), and unauthorized access (7.2%) being remarkably high numbers.
It is worth noting the amount of damage caused by information security troubles in SMEs when viewed by “sales scale.” Looking at the percentage of damage occurrence by company sales scale, a staggering 64.7% of companies with sales of 1 billion yen or less have experienced damage. The smaller the sales scale of the company, the higher the percentage of actual damage occurrence. Since the occurrence of damage can have a significant impact on the management of small and micro enterprises, it is necessary to take sufficient measures.
It is Not Uncommon for SMEs to be Driven to Bankruptcy by Cyber Attacks
According to a survey by a US agency, “America’s Small Businesses Must Take Online Security More Seriously,” approximately 60% of SMEs that have been subjected to cyber attacks go bankrupt within six months. The average cost to a company when a data breach occurs is said to be $117,000 (approximately 13 million yen in Japanese currency). For small organizations with limited capital, it is not uncommon for this financial blow to lead to closure.
Security Risks Faced by SMEs
Lack of Centralized Data Management in Japanese Companies
In Europe and the United States, it is common to use shared files such as Google Drive to centrally manage business data. However, in Japan, it is common to share files by attaching them to emails and saving the files on the PCs (local directories) used by individual employees. If something that can be done with one file is distributed to many people, the security risk increases accordingly.
Insufficient Security Measures on Employee Terminals
Since 2020, companies have been increasingly adopting telework due to the impact of the novel coronavirus. According to a survey announced by the Tokyo Metropolitan Government, 62.7% of companies had introduced telework as of April 2020, an increase of approximately 2.6 times in about one month from 24.0% in March. However, many small and micro enterprises have not been able to keep up with telework, and it is common for them to use private PCs without lending out company mobile PCs. There has been a significant increase in cases where viruses have invaded private PCs without security software installed, affecting the entire company.
[Special Interview] Examples of SMEs Suffering Server Crime Damage
We spoke with Daisuke Tanaka, President of Asueight Advisory Co., Ltd., which promotes the “Digital Forensics Business,” about examples of SMEs suffering damage from cybercrime.

** Reporter: What exactly is “digital forensics”? **
Tanaka: The word “forensics,” which is not commonly heard, means something related to “court.” Digital forensics is the preservation and analysis of evidence against cybercrimes such as unauthorized access, data tampering, and remote control.
** Reporter: What is the percentage of consultations from SMEs? **
Tanaka: More than half of the consultations we receive are from SMEs. Most of the companies have inadequate security measures.
** Reporter: What kind of consultations are you receiving specifically? **
Tanaka: Broadly speaking, there are two types: “cyber attacks” and “intentional information leakage by employees.” In the case of cyber attacks, websites are tampered with, and credit card information is extracted from EC sites. For these damages, we analyze server logs and security tool logs to confirm “when” and “how” it happened, and “what information” was leaked. In the case of information leakage by employees, it may be discovered through reports from other employees or contact from business partners.
** Reporter: It is said that security measures for SMEs are weak, is this true? **
Tanaka: Yes, it is weak. There are some companies that do nothing at all, but I feel that there are many companies that “just have security tools installed without any particular reason.” There are many people in charge who do not understand what security tools can do in the first place, such as “they do not understand the purpose of installing security tools,” “they just installed them as told by the vendor and left them unattended,” and “they have not updated them.” Cyber attacks and information leakage cannot be prevented unless security measures suitable for the company’s business are in place.
** Reporter: Why is it difficult to operate security tools well? **
Tanaka: Are you familiar with the term “endpoint security”? An endpoint means “end” or “terminal.” In other words, it refers to terminal devices such as PCs, smartphones, and tablets. Endpoint security protects the information stored on these devices from cyber attacks.
To give a specific example of this endpoint security, for example, when an alert is issued, a log is uploaded, but in reality, “the person in charge is not looking at it” in many cases. In the first place, security software often takes a wide range of alerts in order to eliminate missed detections of attacks, so the person in charge becomes accustomed to the alerts and misses “really necessary alerts.”
** Reporter: So it becomes like the boy who cried wolf. What do you mean by not having security measures suitable for the company? **
Tanaka: For example, there are cases where a security tool is installed that requires multiple approvals to send an email, even though there are few sales employees who need to contact outside the company. Even with endpoints, it makes no sense to install endpoint security on the PCs of internal employees who do not take their PCs outside the company. The purpose of installing endpoint security is not only to protect against cyber attacks, but also to take logs when a USB is inserted or to restrict its use.
In order to avoid wasting costs, it is necessary to discuss the necessity of each security function. Depending on the company whose main business is internal work, it may be better to focus on the server firewall rather than endpoint security. Security operation requires a balance of “availability” (how much impact it has on operation), “confidentiality” (whether confidentiality is properly protected), and “integrity” (comprehensiveness of the security scope).
** Reporter: Please tell us about an example of an SME being targeted by a server attack and suffering damage. **
Tanaka: The first is the case of Company A, where customer personal information was leaked to the outside due to a cyber attack. Company A did not have insurance, so it incurred tens of millions of yen in damages. Furthermore, the total amount of damage, including security and server replacement costs, attorney fees, our cyber investigation costs, and the establishment of a call center for customer support, exceeded 100 million yen, and Company A’s management was completely undermined.
The second is the case of Company B, where an employee took out confidential information. This is a case where an employee took confidential information from a company PC and put it on a USB. Our company was in charge of restoring the USB and investigating the personal PC. In practice, we suddenly go to the employee’s home with a lawyer, seize all kinds of media such as cell phones, USBs, and PCs, and identify evidence. Although I cannot go into details, the employee who took out the data will incur investigation costs of tens of millions of yen and damages to the company.
** Reporter: Where are the risks lurking? **
Tanaka: The most significant risk may be the naive perception that “our company would never be subjected to a cyber attack.” Listed companies have a responsibility to explain to shareholders, so they are held accountable if a problem occurs, and they need to take strong measures. However, SMEs have less awareness of this, and I have seen presidents who have written off 20 million yen embezzled by accounting staff as tuition fees.
Both the president and the person in charge often “do not feel the risk as their own until something happens.” However, cyber attacks target SMEs with weak security. It is too late after something happens.
Server attacks against companies are rarely reported in the media. Because of this, awareness of security does not change easily. I want you to know that cyber attacks are “not sudden, but are constantly being attacked.” If you look at the logs, you should see that fact for yourself.
** Reporter: How should we approach security measures in our daily lives? **
Tanaka: First, please recognize that cyber attacks and information leakage are “common occurrences” in today’s world. It is important to share within the company “what to do when something happens.”
If you are cyber attacked, we recommend simulating “who to report to,” “when to contact the police,” and “whether you have insurance.”
“Exo Security” That Can Be Easily Operated Even by SMEs Without a Person in Charge
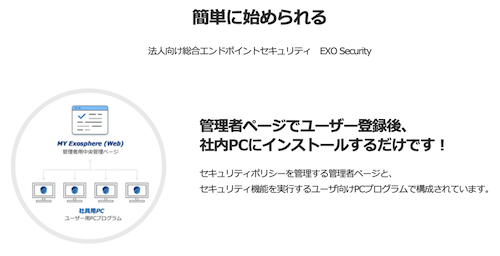
EXO Security protects PCs and mobile terminals from the dangers of malware such as viruses and ransomware that cannot be completely prevented by anti-virus software.
The basic functions include:
・Anti-malware blocking technology that uses artificial intelligence and cloud analysis technology
・Defense against new types of ransomware
・Blocking access to malicious sites
In addition, for personal information protection, there are functions for:
・Detection of unencrypted personal information
・Encryption recommendation or forced encryption
In addition, information leakage countermeasures, program blocking functions, and ease of management are also emphasized, making it a very popular comprehensive service. EXO Security, which provides endpoint security, is called B2BSaaS (Business to Business Software as a Service), and is a subscription service for companies and corporations. Therefore, instead of owning software or systems, you can use the service by paying a fee for the right to use it for a certain period of time.
«EXO Security is 5,000 yen per month for 50 accounts»
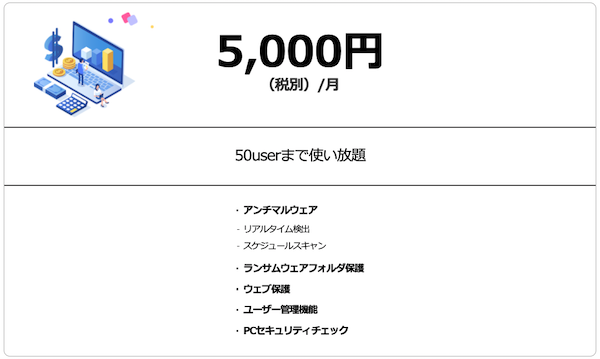
EXO Security is 5,000 yen (tax included) per month for 50 users. Therefore, if 50 people use the service, it will cost only 100 yen per person per month. Other companies charge 24,000 yen per month or 19,300 yen per month for 50 users, which is more expensive than EXO Security, and often have fewer features than EXO Security.
With the functionality of EXO Security, 5,000 yen per month can be said to be the best cost performance.
EXO Security also has a free trial period. If you are a company or corporation that wants to implement perfect security measures and malware countermeasures, please try “EXO Security,” which is currently attracting attention, for free once.
Click here for a list of EXO Security features Industry’s lowest price security service EXO Security Trial application [ ]
For any questions, please contact globalsupport@jiran.com