What is the “Information Security Measures Guidelines” Recommended by the Government for SMEs?

With the promotion of DX, more and more important data is flowing on companies’ networks. Concerns about security risks such as unauthorized access targeting important data are increasing. As the use of digital tools becomes more sophisticated, it is necessary to implement security measures that match the reality.
A challenging aspect of security measures is that threats such as hacking and computer viruses change rapidly. In particular, the cycle of change tends to shorten year by year, and appropriate measures are constantly evolving.
Behind this situation is the fact that, while unauthorized access used to be mostly committed by pranksters, it has now become a business. Hackers are systematically planning profits from crime, which further stimulates the motivation to brush up their techniques. In particular, SMEs that are criticized for inadequate measures, such as the lack of a dedicated security department, are often targeted by hackers.
Therefore, in Japan, the “Information Security Measures Guidelines for SMEs” has been established under the leadership of the Ministry of Economy, Trade and Industry. The information is updated to match changing threats, and the current version, the third edition, was published in 2019.
This time, we will introduce security measures recommended by the government in accordance with the guidelines. SMEs have limited resources to use for measures such as funding and personnel. Let’s start with what we can do first.
1. Four Disadvantages Caused by Insufficient Security Measures
Security risks that should be addressed tend to be postponed because they are difficult to grasp until an incident occurs.
It’s similar to knowing the need for disaster prevention activities and health promotion, but not being able to take action easily. The security measures guidelines list the following items as risks that may occur if security measures are insufficient:
- Financial loss: If customer information is leaked, compensation such as damages will be required.
- Loss of customers: Social reputation is greatly damaged, leading to a loss of corporate competitiveness.
- Suspension of operations: A period of internet shutdown occurs for cause investigation and recurrence prevention measures.
- Impact on employees: A suspicious atmosphere is created in the workplace, leading to a decline in morale and employee turnover.
2. What is the Role of Management in Security Measures?
Security measures require teamwork between management and the field. The “Information Security Measures Guidelines” stipulates the following three principles for the actions required of management:
- Leadership for information security measures lies with management
- Consider security measures at contractors in addition to within the company
- Communicate with stakeholders about information security
In addition, the following seven major frameworks are listed as action items:
- Establish a response policy for the entire organization
- Secure budget and personnel
- Ask the person in charge to consider and implement measures
- Request a review of measures as appropriate
- Develop a system necessary for emergency response and recovery
- Agree on security responsibilities with contractors and external services
- Collect information on the latest trends
3. Comply with the “5 Articles of Information Security Measures” and Make a “One-Star Declaration”
In companies where security awareness has not fully permeated, it may be difficult to implement complete measures all at once.
Therefore, the guidelines list five actions that must be taken.
By implementing these five actions, you can declare your countermeasures using the “SECURITY ACTION One-Star” logo mark provided by the government. Let’s start with basic actions and promote an atmosphere that leads to full-scale movement.
- Keep the OS and software up to date
- Install anti-virus software
- Strengthen passwords
- Review data sharing settings
- Collect information on the latest techniques
4. Self-Diagnose Security Risks with 25 Items
I think there are few people who want to try to understand the current situation when starting new measures.
The guidelines provide a self-diagnosis list of 25 items.
An online site that can be used for checking is also available, and even SMEs with multiple offices can proceed with self-diagnosis remotely.
In addition to the five basic measures, the contents of the list incorporate two perspectives into the diagnostic items: individual employees and the organizational structure.
As the slogan “Can be done in 5 minutes!” suggests, it is a simple list to check with YES/NO.
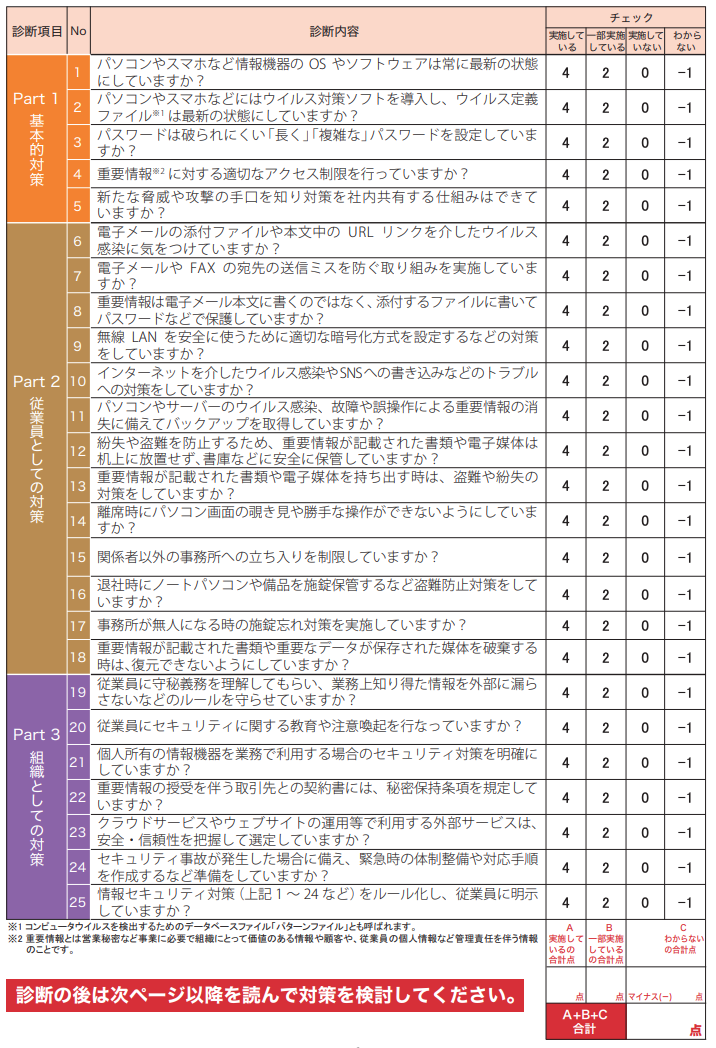
(Source: Information Security Measures Guidelines for Small Businesses, 3rd Edition, Information-Technology Promotion Agency, Japan, 2019)
5. Use the “Explanation Edition” to Take Measures Based on the Diagnosis Results
When considering measures using the results of self-diagnosis, the “Explanation Edition” of the guidelines is useful.
Even companies without personnel familiar with IT can understand the path from realistic measures to security improvement measures.
Countermeasure examples are introduced from a stance of supporting SMEs, and you can specifically understand actions that can be easily executed without spending money or time.
Since the feared damages and accidents are explained, it can also be used as material for requesting cooperation from employees and stakeholders.
Even if you cannot implement measures for all items at once, you can take action by prioritizing them based on your company’s circumstances.
Download here↓
Material: Can be done in 5 minutes! Information Security Self-Diagnosis [ https://www.ipa.go.jp/files/000055848.pdf ](https://www.ipa.go.jp/files/000055848.pdf)
6. The “Information Security Handbook” Template is Convenient for Awareness-Raising Activities!
When moving to the implementation phase for measures determined based on self-diagnosis, the information security handbook template is useful. It is distributed in PowerPoint file format.
The material combines warnings about security risks and the actions necessary for countermeasures, and proper nouns such as company and software names, and contact information such as telephone numbers, are blank.
Creating materials is a burden on the person in charge, but it means that measures can be advanced with minimal effort.
6. Small Start to Full-Scale Security Measures Using Software
When considering security risks, an important change as well as the progress of DX is the rapid increase in remote work.
Terminals that connect to the company’s network are called endpoints and are at the forefront of security risks.
With the spread of remote work, the number of endpoints has also increased rapidly, and it is necessary to control security risks differently than before.
It is said that there are differences in endpoint security measures depending on the size of the company. The smaller the company size, the more likely the measures are to be delayed, and for SMEs, the endpoint security is often limited to the introduction of anti-virus software.
However, just introducing anti-virus software is not enough.
Considering the recent trends in attack methods, in addition to narrowing down the entry point with anti-virus software, EDR (Endpoint Detection and Response) is needed to quickly detect and deal with attacks.
Therefore, many package software with EDR functions are also on sale.
Our EXO Security is the perfect software for a small start to security measures, and its EDR, which is characterized by easy operation, has been highly evaluated.
Software for enterprises tends to be expensive to introduce, but EXO Security is available for 5,000 yen per month for up to 50 users.
EXO Security can help SMEs take the first step in security measures with easy operation and minimal cost.
For inquiries, please contact globalsupport@jiran.com