Countermeasures: Ransomware Infection
Date: 2023.05.19.

In Japan today, the word “Ransomware” has become so famous that there is probably no one who doesn’t know it. Ransomware has become famous because it is the most frequent security incident and causes very large financial damage when it occurs.
This article introduces ransomware, the biggest security risk for companies.
Table of Contents
- Damage from Ransomware Infection
- Reasons for the Rapid Increase in Ransomware Infections
- Downloading unreliable software from unknown sources
- Accessing websites with weak security or illegal audio sites
- Failure to update the OS and software version (security)
- Infection from URLs exchanged while using personal email or messengers
- Ransomware Infection Cases
- How to Prevent Ransomware Infection
- Back up important data to separate removable media on a regular basis
- Do not click on URL links in emails or messages from unknown sources
- Prohibit downloading files from untrusted sites
- Update software promptly
- Use of PC Security Services for Businesses
- How to Respond to Ransomware Infection
- Keep the PC powered on
- Isolate all removable media and shared files connected to the infected PC
- Summary
1. Damage from Ransomware Infection
Ransomware infection causes extremely fatal damage among several security incidents.
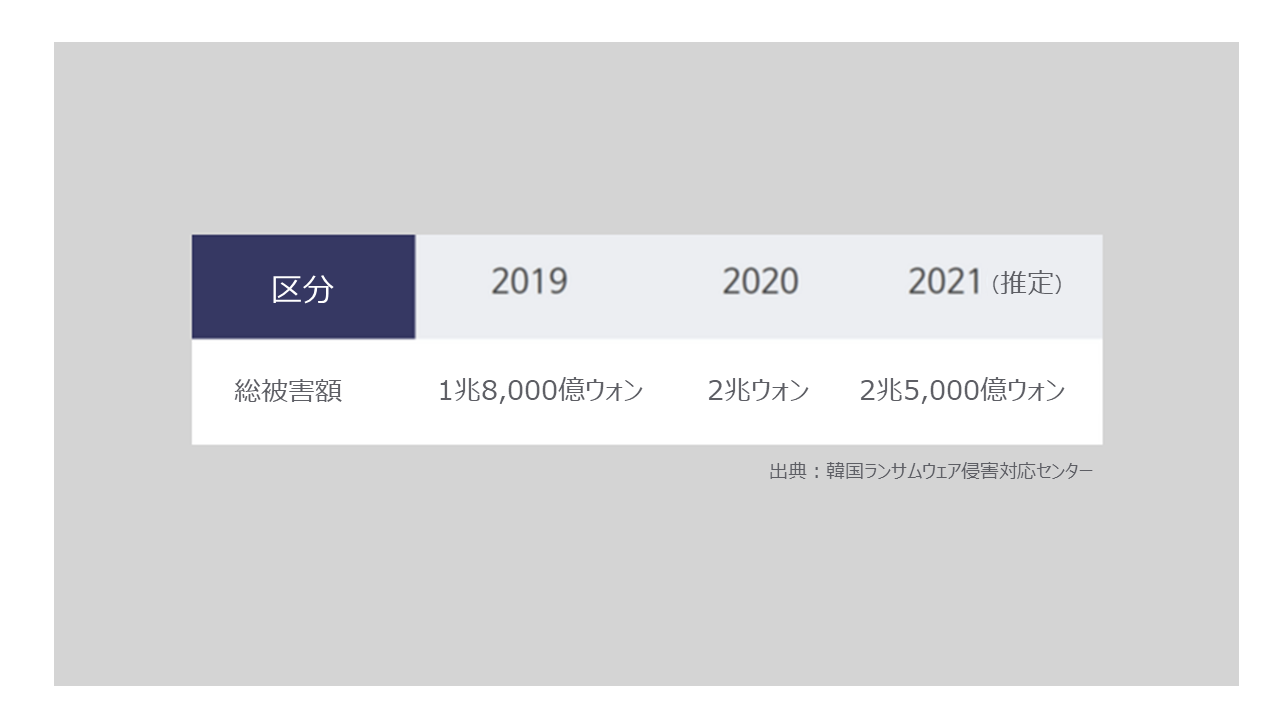
- According to a domestic institution in South Korea, the amount of domestic ransomware damage is about 2.5 trillion won, and the damage increased 6 times during the COVID-19 period. Also, 20% of the companies that were damaged are being driven to the brink of bankruptcy.
- This level of damage is a more serious figure than the international economic downturn that has occurred since COVID-19.
2. Reasons for the Rapid Increase in Ransomware Infections
Experts say that during the COVID-19 pandemic, companies were forced to respond quickly to telecommuting, and the number of business environments utilizing the cloud increased without a complete information security infrastructure, resulting in security vulnerabilities.
Checking the main routes of ransomware infection reveals the following four routes:
2-1. Downloading unreliable software from unknown sources
In recent years, there have been frequent reports of connections to phishing sites that can infect malicious code and ransomware from free software that can be used in companies and businesses.
- In particular, ransomware and malicious code are distributed through software that is often used for work, such as video editing, photo editing, file extension conversion, and automatic capture, making it easy for companies to become infected.
2-2. Accessing websites with weak security or illegal audio sites
There have been frequent cases of employees becoming infected by using audio sites through their company PCs or entering the wrong website URL address and accessing it.
- In particular, extra caution is needed because phishing is done by creating a URL address that is very similar to the URL address of a famous website that is often accessed during work, and the UI is also very similar to the target website. If the PC does not have security measures in place, it may become infected with ransomware simply by accessing the site.
2-3. Failure to update the OS and software version (security)
OS and software updates include not only function updates and error fixes, but also information security updates.
- Therefore, if you do not update for a long time, the security of the OS and software will be weakened, which will cause security vulnerabilities.
2-4. Infection from URLs exchanged while using personal email or messengers
Personal messengers and emails are often used to exchange personal and informal materials and URLs because they are not related to work.
- In this case, there is a high possibility of accessing the above-mentioned websites with weak security or downloading unreliable materials, which can cause ransomware infection of company PCs.
3. Ransomware Infection Cases
A Korean mobile game company had an incident in which its server was infected with ransomware during the transfer of a server for its online game service, forcing it to suspend the entire game service.
- Although the game was so popular that it was ranked in the top rankings, the entire online game business was suspended due to the fatal attack through ransomware.
In this way, 93% of ransomware infections that can shut down an entire business occur in startups and small and medium-sized enterprises.
- In general, information security infrastructure is not as well-established as in medium-sized and large companies, making them easy targets for hackers.
4. How to Prevent Ransomware Infection
4-1. Back up important data to separate removable media on a regular basis
Important data must be backed up to an external hard disk or USB according to the convenience of management to prepare for data loss in the event of a ransomware infection.
- If you use cloud storage capacity, additional data leakage may occur in the event of a ransomware infection, so it is important to secure a separate device.
4-2. Do not click on URL links in emails or messages from unknown sources
For unfamiliar links, it is necessary to check the source before clicking.
- Even simple access can cause ransomware infection, so we recommend accessing after checking the source.
4-3. Prohibit downloading files from untrusted sites
Ransomware can be infected from music files, video files, and even image files.
- Therefore, it is necessary to check whether the site is reliable before downloading.
- Also, in recent years, downloading sound source files or video files through YouTube may lead to ransomware infection, so it is necessary to check whether the file is reliable.
4-4. Update software promptly
Although it varies with each update, software updates usually include security updates.
- Therefore, prompt software updates are a way to apply the latest security technology to the software you use.
5. Use of PC Security Services for Businesses
The above four security rules can reduce the probability of ransomware infection, but they not only reduce business efficiency, but also make it easy to become infected with ransomware because there is no system to protect the company’s intangible assets in the event of a cyber attack.
Therefore, it is necessary to establish an in-house information security policy through PC security solutions for businesses.
“Endpoint security for corporations that can solve PC security for corporations all-in-one”
- Anti-malware
- Ransomware prevention
- In-house PC vulnerability check
- WEB protection
- Establishment of security policy through central management
6. How to Respond to Ransomware Infection
6-1. Keep the PC powered on
Users may misjudge the ransomware infection as a system error and restart it.
- Some ransomware may automatically delete files on the PC if the PC is shut down while a message indicating infection and requesting money is displayed.
Therefore, it is desirable to keep the PC powered on and understand what type of ransomware has been infected and how to respond.
6-2. Isolate all removable media and shared files connected to the infected PC
If removable storage media such as USB or external storage media such as external hard disks are connected to the infected PC, the files in the storage media may also be encrypted.
Therefore, the connected media must be separated quickly.
If there are shared folders on the infected PC, the folders may also be infected with ransomware, so it is important to quickly unshare them.
Summary
Ransomware can drive you to the brink of bankruptcy once infected. Be sure to check the methods to prevent it and protect your important corporate assets!
Contact: globalsupport@jiran.com