How to Protect Personal Information in Outsourcing and on Business PCs
Hello everyone,
This is the EXO Security Support Center.
In recent years, we often see news about corporate personal information leaks.
This indicates that there are a significant number of incidents involving the leakage of customer personal information at companies.
Especially for companies entrusted with personal information, attention should be paid not only to the servers where services are operated but also to the user PCs that handle customer information.
Have you ever wondered how to prevent customer information from being leaked from user PCs at entrusted companies?
Therefore, this time, we would like to introduce three of the most common routes of customer information leakage at entrusted companies and how to manage personal information on business PCs.

- Inadequate Internal Information Management
: User carelessness within the company, unauthorized user access, and security system flaws. - External Hacking Attacks
: Hackers infiltrate the company’s network or system and leak information. - Sharing with Third Parties
: A third party with whom the company shared information neglects information management and leaks the information.
In order to prevent such leaks, companies must take proactive measures for personal information protection and manage it continuously.
As specified in the “Personal Information Protection Act” and “Technical and Administrative Safeguards for Personal Information,” companies have a duty to safely store the personal information of customers (individuals or companies), and if they violate the relevant laws and regulations, they will be subject to fines and other penalties.
Therefore, companies entrusted with customer personal information must periodically check at least once a year whether they are safely managing personal information based on the “Personal Information Protection Checklist for Entrusted Companies.”
Now, let’s examine what items are included in the “Personal Information Protection Checklist for Entrusted Companies” and how to prepare for them.
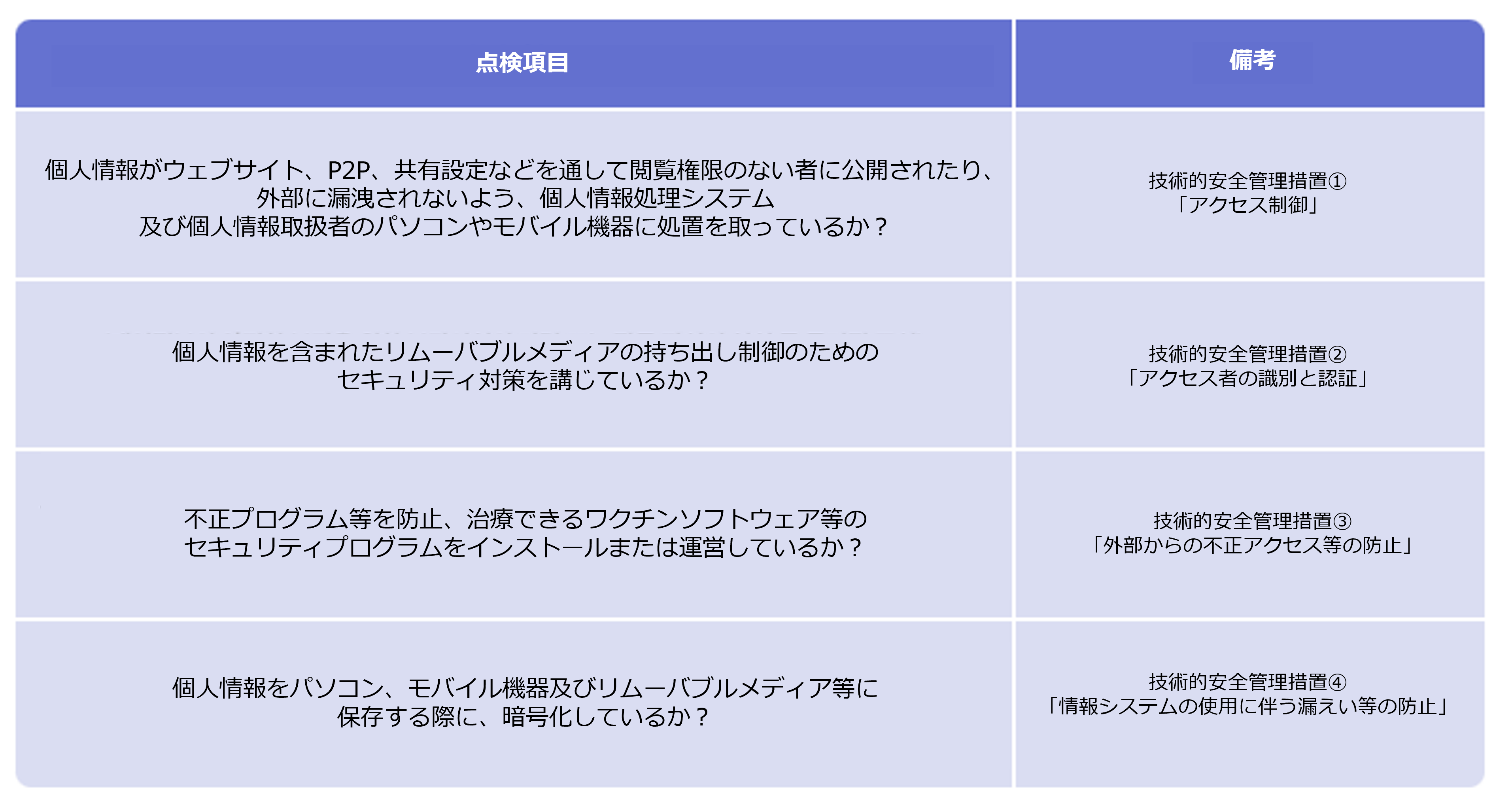
Personal Information Protection Checklist for Entrusted Companies (PC)
There is an obligation to manage and supervise the protection of personal information by external contractors, and it may be necessary to prepare supporting documents for how actual protection measures are being implemented.
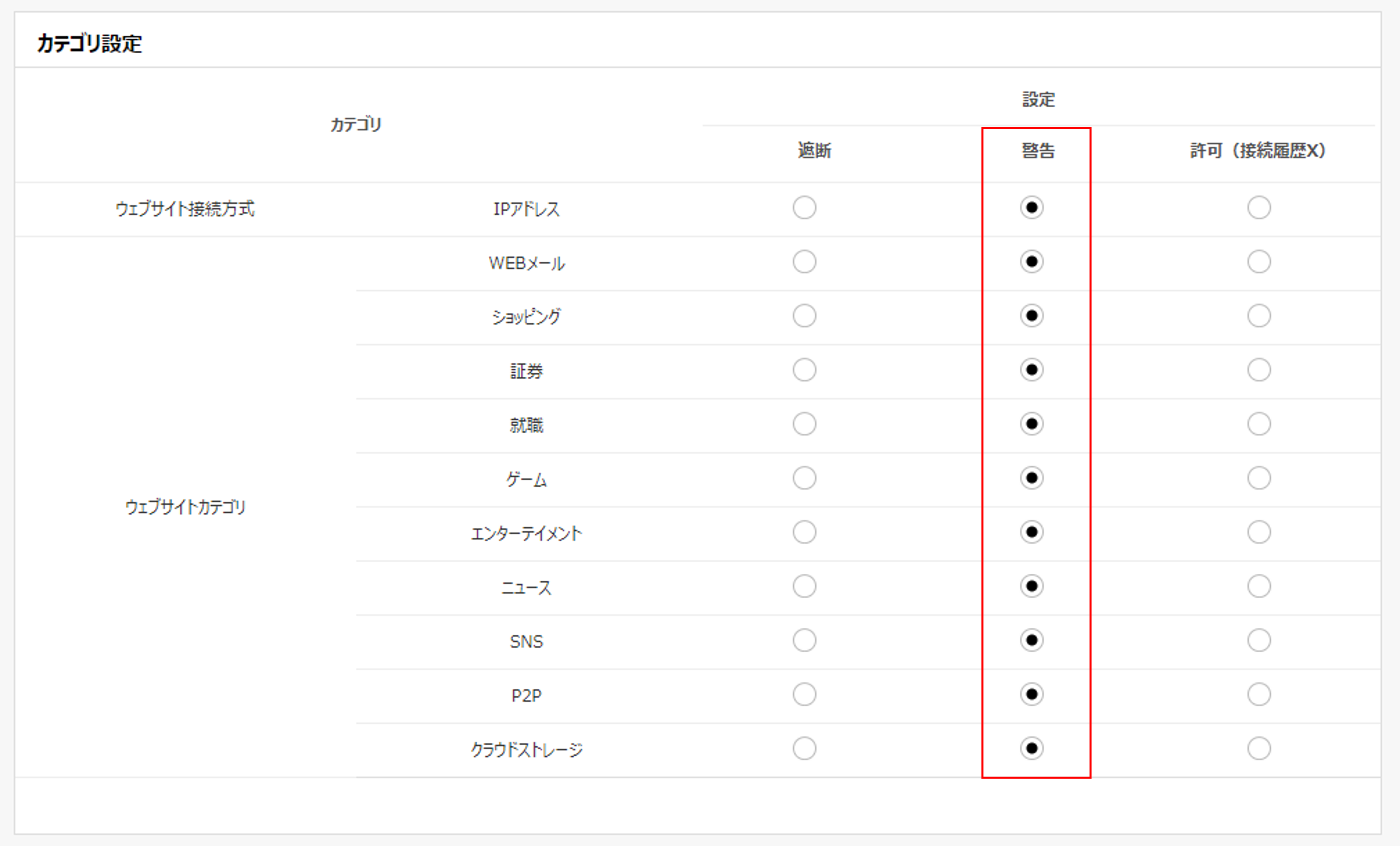
Do you know how well “EXO Security” is prepared regarding personal information protection?
For those of you who have never checked personal information protection and don’t know where to start or how to prepare, we would like to introduce some of the features of “EXO Security” that can systematize personal information protection.
Managing Personal Information on Your Computer


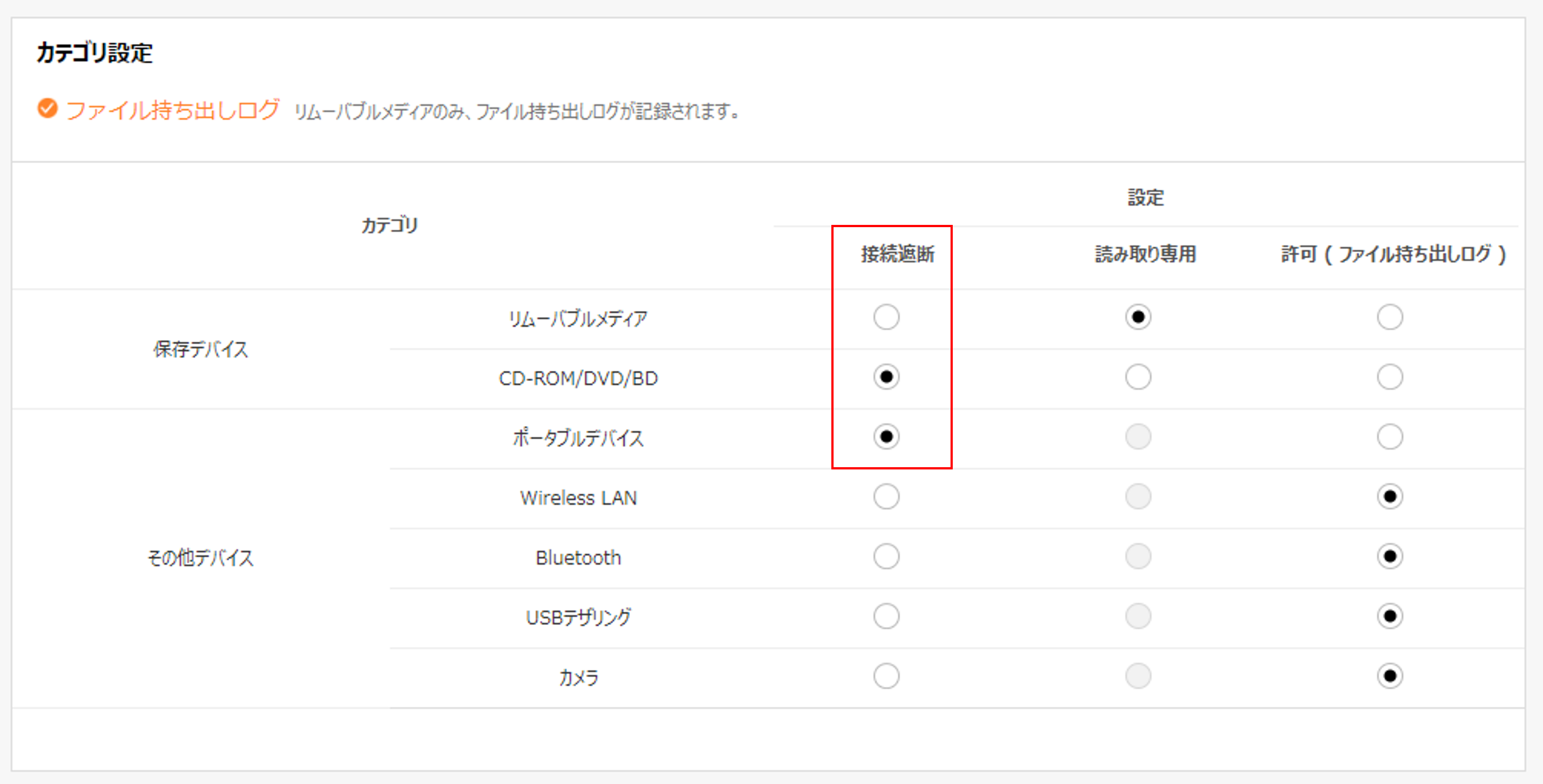
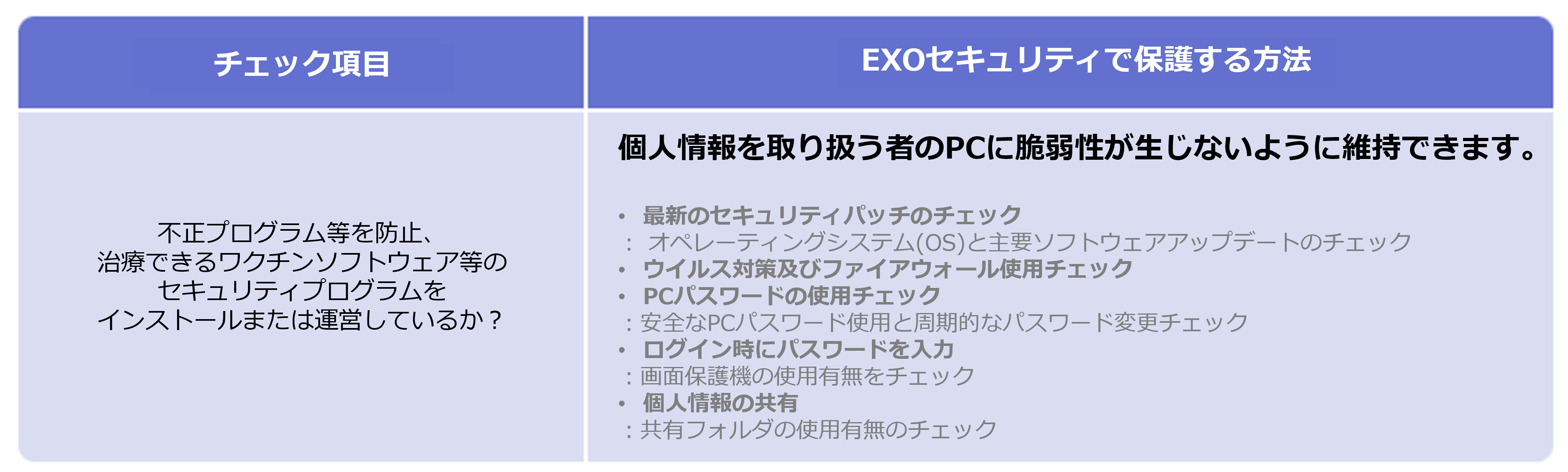
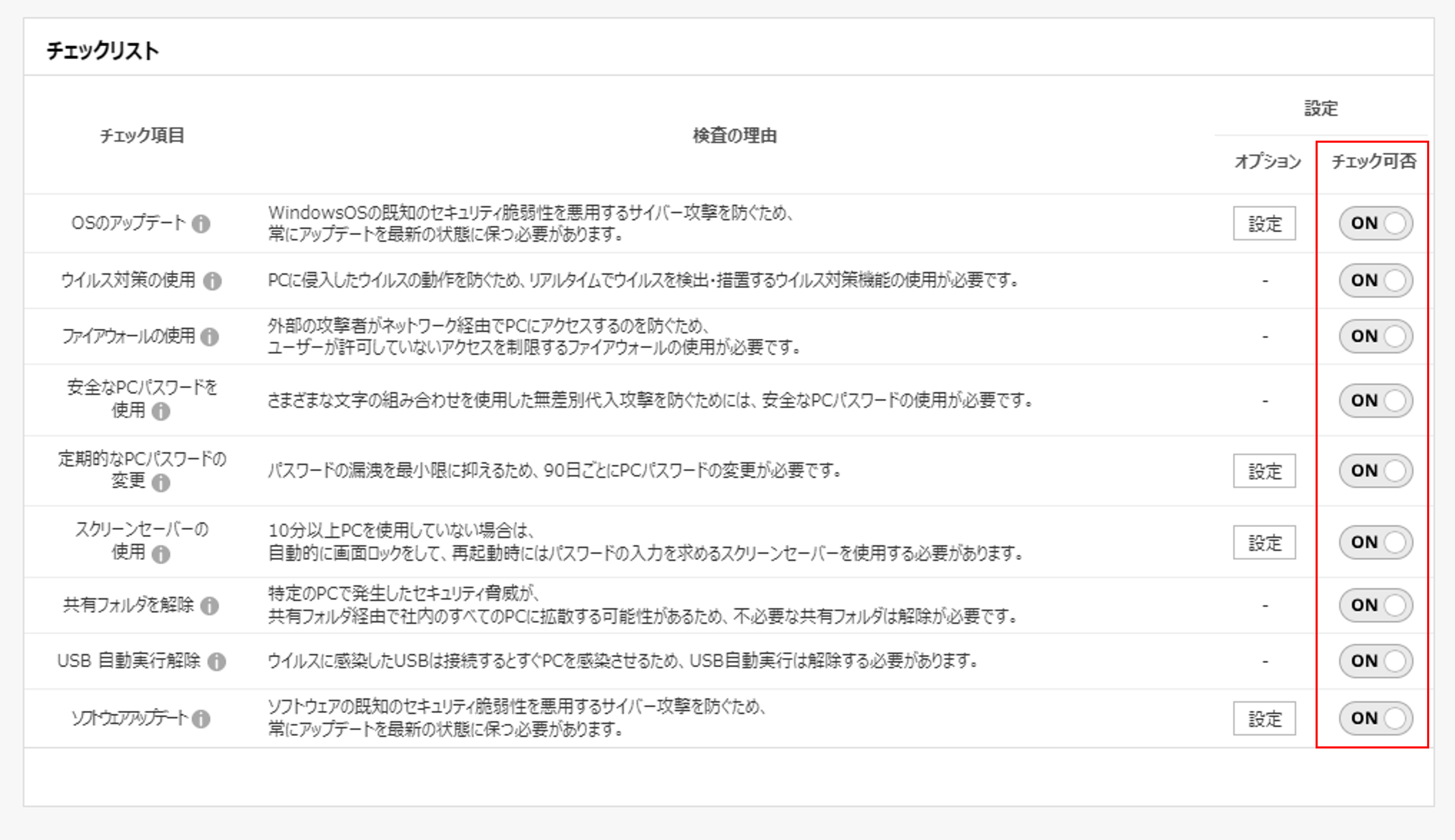

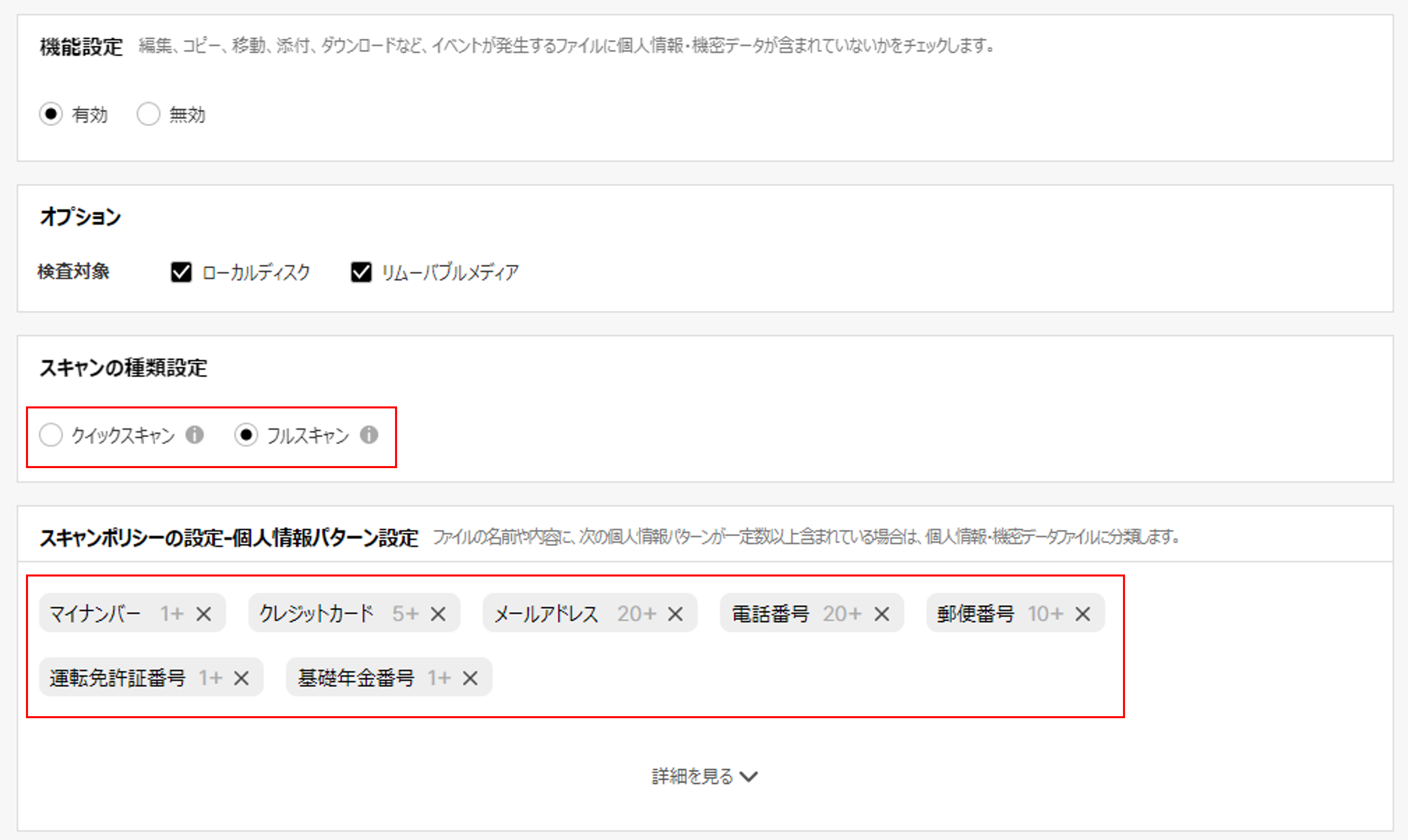
Even a small mistake is not allowed in personal information management, but with “EXO Security,” anyone can easily protect corporate personal information, even without a dedicated security professional!
In addition, “EXO Security” has many other useful features!
Please refer to the following pages as well.
https://exosp.net/personal-information-protection
https://aware-headphones-7d4.notion.site/EXO-c6a8528b957c425fa8f175992ebd1941
* The above page can also be accessed from the User Guide in the lower left corner of the administrator page.
For inquiries, please contact us here:
■ Inquiries by email: globalsupport@jiran.com